CS 605 Info Coding & CRYPTOGRAPHY
SUMMER 2020
Instructor: Dr. Levent ERTAUL
Office:
SF 569
Phone: (510)
- 885-3356
Email: levent.ertaul@csueastbay.edu
Web: http://www.mcs.csueastbay.edu/~lertaul
Class Schedule:
Section
1 Lecture: Online
Course Requirements
This class will be held on-line. The instructor will provide PowerPoint lectures with accompanying audio-video tracks and transcript. Lecture videos and audios (mpeg) can be downloaded to iPod or iPhones.
The final exam & Midterm Exam will be held ONLINE
Major announcements related to class will be posted on my web site. Check regularly announcement section from class web page.
Students will receive the solutions of assignment problems and personal messages from their Horizon E-mail accounts. So please check and clear your horizon e-mail accounts regularly.
Students will use TURNITIN application in blackboard to submit their assignments. FYI, TURNITIN application has plagiarism filter built in . When students submit their assignments TURNITIN application prepares an ORIGINALITY report. Students can see this report immediately. Originality reports which have greater then and equal to %40 WILL NOT BE ACCEPTED. These assignments will get 0 points. If the originality report is higher then %80, instructor will file plagiarism report.
Students will submit their Homeworks on time. Students will have TOTAL 3 DAYS late submission days. They can use this 3 days partially or whole whenever they need it. When they use their 3 days for late submmission -25 points will be cut for one day late Homeworks. After 3 days late sunbmmisons used, Homeworks which are late WILL NOT BE ACCEPTED. These homeworks will get 0 points. E-mail submissions WILL NOT be accepted. These homeworks will get 0 points. Scanned and handwritten homeworks WILL NOT be accepted. Cropped Screen Shots WILL NOT be accepted (CrypTool assignments)
During office hours, students can chat with the instructor for their questions by using SKYPE. Skype ID: CSUEBLERTAUL . (visit http://www.skype.com to get a free account)
Course Description:
Cryptographic theory with applications to data security. Classical Encryption techniques such as Substitution, Transposition Techniques, Steganography, Block ciphers and DES, AES, Triple DES, Blowfish, RC5, RC4. Confidentiality with Symmetric Encryption. Publickey Encryption and Hash Functions: RSA, Diffe-Hellman Key exchange, Elliptic Curve Cryptography, Message authentication, MD5, SHA, RIPEM-160, HMAC and finally Digital Signatures and authentication Protocols.
Prerequisites:
- CS 301 or CS 601
Required Text:
Cryptography
and Network Security: Principles and Practice, 7th Edition
Published by Pearson
Copyright
© 2017
Published
Date: Feb 24, 2016
·
Optional Text:
Introduction to Cryptography with Coding Theory, 2/E
Wade Trappe
Lawrence C. Washington
ISBN-10: 0131862391
ISBN-13: 9780131862395
Publisher: Pearson
Copyright: 2006
Format: Cloth; 592 pp
Published: 07/15/2005
CS605 STUDENT LEARNING OUTCOMES
Students will be able to
1. Describe key network security requirements of confidentiality, integrity and availability
2. Discuss types of security threats and attacks.
3. Understand Network Security Model
4. Understand Security services and Mechanisms
5. Understand the symmetric Cipher Model
6. Present an overview of the Feistel Cipher
7. Present main concepts of symmetric cryptography (DES, BLOWFISH, 3-DES, RC4, RC5 and AES algorithms)
8. Present basic concepts in Number theory and Finite Fields
9. Understand the basic Cipher Mode of Operations (ECB, CBC, CFB, OFB, CM)
10. Present main concepts of asymmetric cryptography (RSA, Diffe-Hellman, ECC)
11. Discuss key distribution Techniques
12. Understand the operation of HASH & MAC Functions
13. Understand the operation of SHA-128, whirlpool, HMAC & CMAC algorithms
14. Understand the Digital Signatures (RSA, DSS)
Course
work and Grading:
|
Homework (includes Cryptool Projects) |
30% |
|
Midterm Exam |
35% |
|
Final Exam |
35% |
|
|
|
Final Grades are based on total course %.
Final grades are assigned based on total points
accumulated. Students earning similar point totals will receive similar
letter grades based on the following
approximate
distribution.
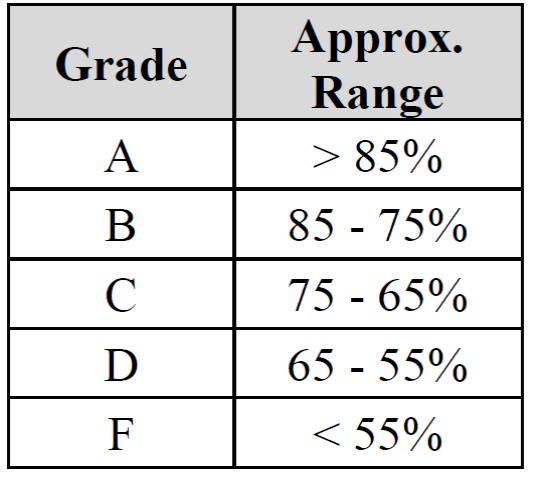
Plus and minus grades will be assigned as appropriate
within the given categories. The
instructor reserves the right to adjust the grade distribution up or down
as needed based on the distribution of points in class to ensure parity in
grading.
University policy states that no final exam may be taken before or after the scheduled time for any reason.
Academic Dishonesty
By
enrolling in this class, the student agrees to uphold the standards of
academic integrity described in the catalog at
http://www.csueastbay.edu/ecat/current/i-120grading.html#section12.
-
Information on what to do in an emergency situation (earthquake, electrical outage, fire,extreme heat, severe storm, hazardous materials, terrorist attack) may be found at http://www.aba.csueastbay.edu/EHS/emergency_mgnt.htm. Please be familiar with these procedures. Information on this page is updated as required. Please review the information on a regular basis.
-
If you have a documented disability and wish to discuss academic accommodations, or if you would need assistance in the event of an emergency evacuation, please contact me as soon as possible. Students with disabilities needing accommodation should speak with the Accessibility Services.
-
Title IX and CSU policy prohibit discrimination, harassment and retaliation, including Sex Discrimination, Sexual Harassment or Sexual Violence. CSUEB encourages anyone experiencing such behavior to report their concerns immediately. CSUEB has both confidential and non-confidential resources and reporting options available to you. Non-confidential resources include faculty and staff, who are required to report all incidents and thus cannot promise confidentiality. Faculty and staff must provide the campus Title IX coordinator and or the DHR Administrator with relevant details such as the names of those involved in an incident. For confidential services, contact the Confidential Advocate at 510-885-3700 or go to the Student Health and Counseling Center. For 24-hour crisis services call the BAWAR hotline at 510-845-7273.
For more
information about policies and resources or reporting options, please visit
the following websites:
http://www.csueastbay.edu/af/departments/risk-management/investigations/registercomplaints.html
